
AI that reads your logs, enriches every signal, and tells your team what to do next.
ObsidianOne is an AI-enriched incident engine: it turns noisy telemetry into prioritized incidents, high-level threat summaries, and actionable playbooks — giving SOC managers a top-down view, analysts instant context, and responders precise guidance.
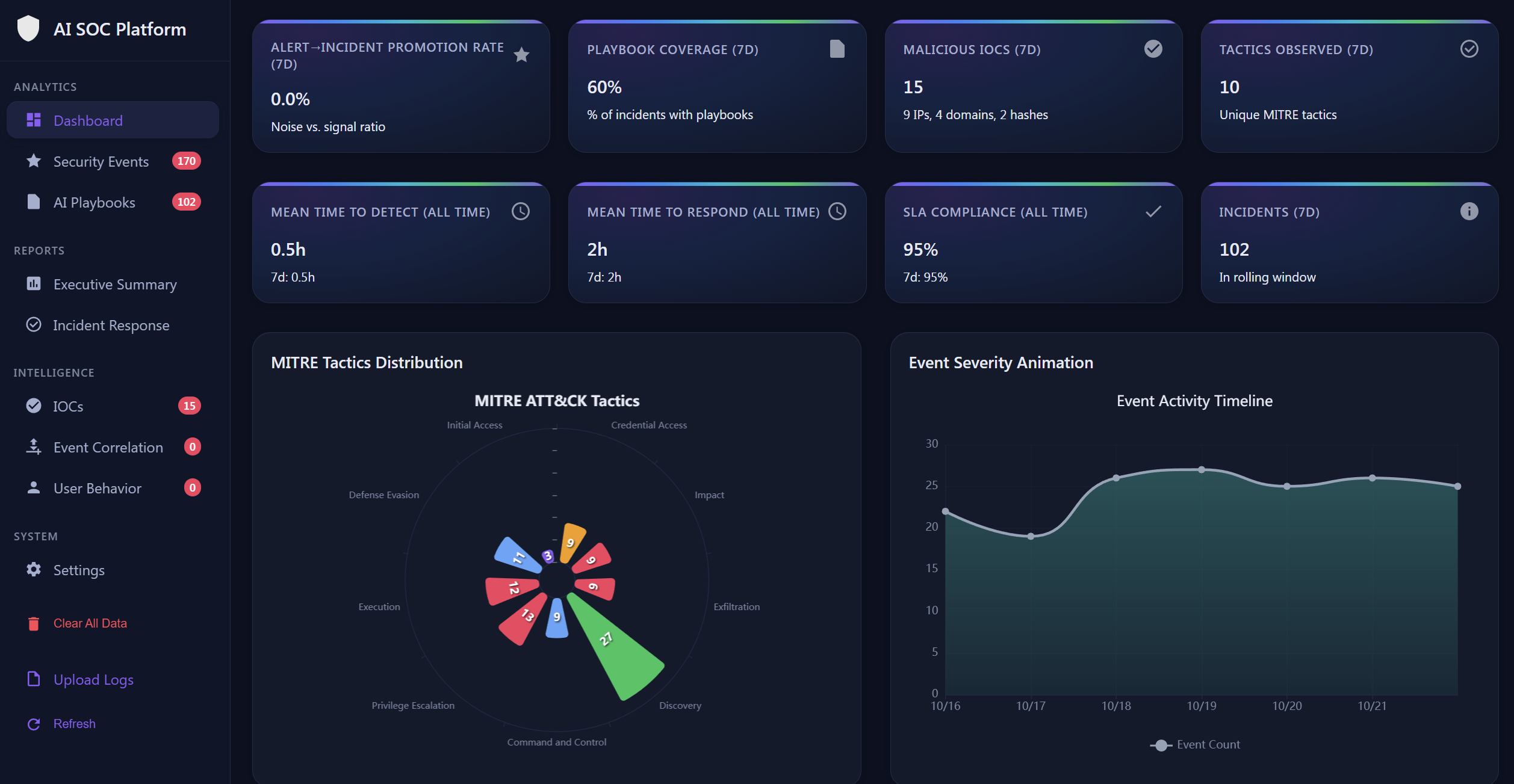
AI-Powered Enrichment at Every Layer
Our AI engine automatically enriches every log event with threat intelligence, MITRE ATT&CK mappings, behavioral scoring, and cross-event correlation — transforming raw telemetry into actionable security incidents with executive-ready summaries and step-by-step response playbooks.
AI Threat Summary: Coordinated encryption behavior on 3 hosts targeting finance shares. Pattern matches human-operated ransomware. Requires immediate isolation, token revocation, and backup integrity verification.
- MITRE: T1486 (Impact), T1059 (Execution), T1078 (Valid Accounts)
- Scope: 3 endpoints · 2 privileged accounts · 1 high-value share
- Next steps (high level): Contain → Hunt lateral movement → Validate backups → Exec update.
The AI generates a dedicated, environment-aware runbook for responders: containment, investigation focus, eradication steps, and recovery validation — without polluting the analyst-facing event stream.
AI enrichment reduces noise by correlating signals, ranking severity, and surfacing incidents your team should care about first.
Live overview of campaigns, risky identities, and affected assets across tenants — built for Next-Gen SOC leaders.
Each major incident ships with an AI-authored response track: who should act, what to verify, and how to close it confidently.
Key capabilities for a Next-Gen SOC
ObsidianOne combines AI enrichment, multi-tenant visibility, and operational playbooks in one focused product — built for SOC managers, analysts, and MSSPs who need outcomes, not another dashboard.
- • Top-down incident and tenant view in one place.
- • AI-written summaries translate technical detail into risk language.
- • MITRE-aligned reporting for execs and auditors.
- • Usage & cost insights for planning and client billing.
- • AI-enriched threat summaries for each key event/cluster.
- • Auto-linked related events, users, IPs, and assets.
- • Clear “why this is risky” context, not walls of JSON.
- • Seamless handoff to AI playbooks when escalation is needed.
- • Native multi-tenant design for clean client separation.
- • Playbooks tailored per tenant & service level.
- • Exportable incident reports your clients actually understand.
- • Aligns with your existing tools instead of replacing them.
How it works end-to-end
A clear pipeline from raw logs to AI-enriched, actionable incidents — no black box, just structured help.
Connect S3, upload CSV/JSON, or wire SIEM exports. Events automatically tagged by tenant and source.
Normalize, de-duplicate, map to MITRE ATT&CK, and enrich with context & indicators — AI-ready data.
AI generates concise threat summaries: what happened, why it matters, scope, and recommended response track.
Responders use dedicated AI playbooks to contain, eradicate, and recover. Integrate with tickets/chat to operationalize Next-Gen SOC workflows.
Security & trust by default.
AI enrichment doesn’t mean chaos. The architecture is opinionated, boring-in-the-right-ways, and AWS-native.
- ◆ Tenant-aware isolation at every layer.
- ◆ Hosted on AWS with your regional & IAM guardrails.
- ◆ Secrets via AWS Secrets Manager, no hard-coded keys.
- ◆ Aligns with SOC 2 / ISO 27001 style controls & logging.
- • S3 for ingestion & artifacts
- • App Runner for stateless API & UI backend
- • CloudFront for secure global delivery
- • DynamoDB & S3 for durable, auditable storage
We walk your security & platform teams through data flows and residency during onboarding so everyone signs off confidently.
Simple, transparent pricing
Volume- and tenant-based pricing that covers infra and AI enrichment while staying 40–70% below typical “AI SOC” add-ons from legacy vendors.
Founders Edition discounts apply to Professional & Enterprise tiers for early design partners.
Up to 50 GB logs / month · 1 tenant
- • AI Threat Summaries
- • Core dashboards & exports
- • MITRE ATT&CK mapping
- • Email support
Up to 250 GB logs / month · Multi-tenant
- • AI Summaries + AI Playbooks
- • Multi-tenant & client management
- • Usage & cost visibility
- • Priority onboarding & support
Up to 1 TB logs / month · Unlimited tenants
- • All Professional features
- • Advanced integrations (ITSM, SIEM, chat)
- • Premium support & roadmap input
- • Optional dedicated environment
How we compare
Same core outcomes as big vendor AI SOC add-ons — AI enrichment, faster triage, clearer incidents — without lock-in, hidden SKUs, or overbuilt bloat.
| Capability | ObsidianOne | Big Vendor AI Add-ons* |
|---|---|---|
| Pricing model | Simple tiers, usage-aligned | Complex, contract-bound, upsell-heavy |
| Target users | MSSPs & SOCs of any size | Primarily large suite customers |
| AI threat summaries | Included on all plans | Often gated or limited |
| AI enrichment depth | Per-incident narrative + playbooks | Inline hints, less prescriptive |
| Multi-tenant support | First-class, MSSP-native | Varies; often secondary |
| Infra alignment | AWS-native, minimal moving parts | Coupled to vendor stack |
| Time to value | Hours / days | Weeks / months |
*High-level comparison based on typical patterns of major AI-enhanced SOC/SIEM offerings.
Is ObsidianOne right for my SOC?
If you check a few of these boxes, you’re exactly who we built this for:
- ☑ You're running a lean SOC or MSSP and drowning in alerts, not outcomes.
- ☑ You want AI enrichment and Next-Gen SOC capabilities without a 7-figure contract.
- ☑ You need clear incident narratives for executives, clients, or regulators.
- ☑ You manage multiple environments or customers and need clean tenant separation.
- ☑ You prefer AWS-native, auditable architecture over black-box platforms.

- • Review your current logging & detection landscape.
- • Walk sample logs through AI enrichment & summarization.
- • Show multi-tenant views (if you’re an MSSP or multi-env org).
- • Map cost vs. your existing stack, including Founders Edition options.
The goal is simple: prove in one session that ObsidianOne can reduce noise, sharpen response, and fit your environment without friction.
See ObsidianOne on your logs.
Tell us a bit about your environment and we’ll walk through AI enrichment, incident summaries, and playbooks tailored to your SOC or MSSP.
